The Many Ways We Get Information - Understanding The Core Of 'Get'
We are, in a way, always on the hunt for pieces of knowledge, for bits of understanding that help us make sense of things. Whether it's finding out how a certain program works, or figuring out where a particular file might be hiding, or even just trying to grasp the meaning of a common word, our days are filled with moments where we look to "get" something. This pursuit of information, you know, it's a fundamental part of how we interact with the world around us.
Think about it for a moment. From the simplest daily inquiries to more involved technical investigations, the act of gaining possession of facts, figures, or answers is pretty much constant. It's like we're always trying to connect the dots, always reaching out to pull in what we need to move forward. This idea of "getting" something, of acquiring a piece of the puzzle, really shapes how we approach problems and how we build our knowledge.
The word "get" itself, as a matter of fact, is one of those incredibly versatile terms in our language. It pops up in so many different situations, sometimes meaning to fetch, other times to receive, or even to cause something to be in a certain state. We use it to talk about obtaining physical things, but also to describe the process of gathering abstract details, like data from a computer system or an explanation from a person. This adaptability, you see, makes it a truly fascinating word to look at.
- Mia Khalifa Tongue Out
- Lily Newhouse Poker Husband
- Syren De Mer Selfie
- Maisey Monroe Onlyfans
- Mature Chubby Homemade
Table of Contents
- What Does It Mean to Get a Load of Information?
- Getting the Details from Computer Systems
- How Do We Get Data for Analysis?
- Getting Network and Device Insights
- Is Getting Information Always Straightforward?
- The Process of Getting Access and Credentials
- What About Getting Software Paths and User Groups?
- The Broad Meanings of 'Get'
What Does It Mean to Get a Load of Information?
When someone says they need to "get a load of" something, they often mean they need to take in a substantial amount of information or observations. It's about absorbing a collection of facts or an entire situation. For instance, in the world of computing, you might want to gather a full collection of all the files within a particular folder and its nested compartments. This kind of task involves asking the computer system to provide a comprehensive list, rather like asking for a complete inventory. You're not just looking for one item, but for a whole body of items, so to speak.
This quest for a full picture, you know, often begins with trying out commands or settings. People might try using system prompts, perhaps looking at the built-in help guides for directions. Sometimes, it's about experimenting with configuration settings to see what details they reveal. The goal is to discover a straightforward way to obtain not just one piece of information, but a collection of related facts, like both a name and an email address tied together. It’s about making sure you capture the whole story, or at least a significant portion of it.
Getting the Details from Computer Systems
A big part of working with computers involves asking them to hand over specific pieces of information. For example, if you're working with data collections, like those in a pandas structure, you might need to figure out just how many rows of entries are contained within. This is a very common task for anyone looking to understand the size or scope of their data. There are various ways to count things in these data structures, and it often depends on what exactly you're trying to measure. Basically, it's about getting a precise count of elements.
- Obsessed With Zoe Nude
- Boynextdoor Photocard Template
- Trey Songz Tweet
- Debby Ryan 9 11
- Womandriven Doris Onlyfans
Another common need is to find out the network address of a device that is directly linked to a specific connection point. Imagine you have a computer and it’s plugged into a network cable; you might want to identify the unique numerical label of another machine connected to that same wired path. This involves asking the system to report on its network connections and the identities of other devices it can communicate with. It’s about making sure you can locate and identify other machines on your local setup, so you can, like, interact with them.
How Do We Get Data for Analysis?
When it comes to working with data, especially for analysis or processing, the first step is always to bring that information into your workspace. For instance, if you need to fetch data from a web service that requires special access, you might have to make a request that includes a unique security key. This is a bit like showing an identification card to get into a restricted area. While some tools make this process fairly simple, figuring out how to do it within your own custom programs can sometimes present a bit of a challenge. It’s about understanding the specific steps to obtain the necessary data for your project.
To make these kinds of requests, people often use specialized software components that handle the security aspects. These components help create a secure connection and then use your unique identification details to request an access pass from the information provider. The provider, in turn, checks your credentials and, if everything lines up, gives you a temporary pass that allows you to collect the data you need. So, really, it’s a systematic way to ensure that only authorized parties can retrieve sensitive information.
Getting Network and Device Insights
Knowing the names of computers on a network, especially when they are not physically in front of you, is quite useful. You might have only a network address and need to figure out the corresponding machine name. This kind of task has been a point of interest for many years, with people often looking for the most effective approach to gather this information from a distance. It involves querying the network to identify devices by their assigned names, which is sometimes easier said than done.
Similarly, when managing user accounts, it's often helpful to know which groups a particular individual belongs to. This helps in understanding their access privileges and roles within a system. There are often built-in tools or commands that can provide this kind of membership information. It's about getting a clear picture of an individual's affiliations within the organizational structure, so you can, you know, manage permissions appropriately.
Is Getting Information Always Straightforward?
Sometimes, the path to obtaining information isn't a direct one. You might be looking for a specific piece of software on your computer, say, where your Python program is installed on a Windows machine. While some installations might put it in a very common spot, others might place it elsewhere. So, finding that exact location can sometimes involve a bit of searching or using system commands that report on installed applications. It's not always as simple as just looking in one obvious place, you know.
Even when you have a way to get the information, the way it shows up might not be exactly what you need. You might receive a jumbled collection of data that requires some shaping or arranging to make sense of it. This is where formatting the output comes into play. You have to take the raw information and put it into a more readable or usable form. So, in a way, getting the information is one step, and then making it usable is another, just as important, step.
The Process of Getting Access and Credentials
Securing access to online services or protected data often involves a structured process of obtaining credentials. This usually means setting up a session that can communicate securely with the service provider. For example, using a library specifically for authentication helps in creating a secure connection. This connection then allows you to request an access token, which is essentially a digital key that grants you permission to use the service. It’s a bit like getting a special pass to enter a private club.
The details needed to get this access token typically include the address of the service provider, a unique identifier for your application, and a secret code that verifies your identity. These pieces of information are given to the service, and if they match what the service expects, you are granted the token. This process, as a matter of fact, ensures that only legitimate applications can interact with the service, keeping things secure.
What About Getting Software Paths and User Groups?
Finding where a particular software application lives on your computer system can be a common task, especially for those who work with programming or system administration. You might be trying to locate the precise folder where your Python interpreter is installed on a Windows system, for instance. This information is often needed for setting up development environments or for running scripts. Sometimes, you have to use specific system commands or tools that are designed to report on installation locations, so you can, like, point your other programs to the right place.
Similarly, understanding the memberships of a particular user within various system groups is a frequent requirement for managing permissions and security. Knowing which groups a person is a part of helps to determine what resources they can access and what actions they can perform. There are usually built-in system tools or scripting commands that allow you to query this information directly. It's about getting a clear picture of a user's privileges, which is, you know
- Neyleen Ashley Of
- Dr Jimmy Sullivan
- Mature Chubby Homemade
- Molly Pills Actress Age
- Kayla Butternutgiraffe Onlyfans
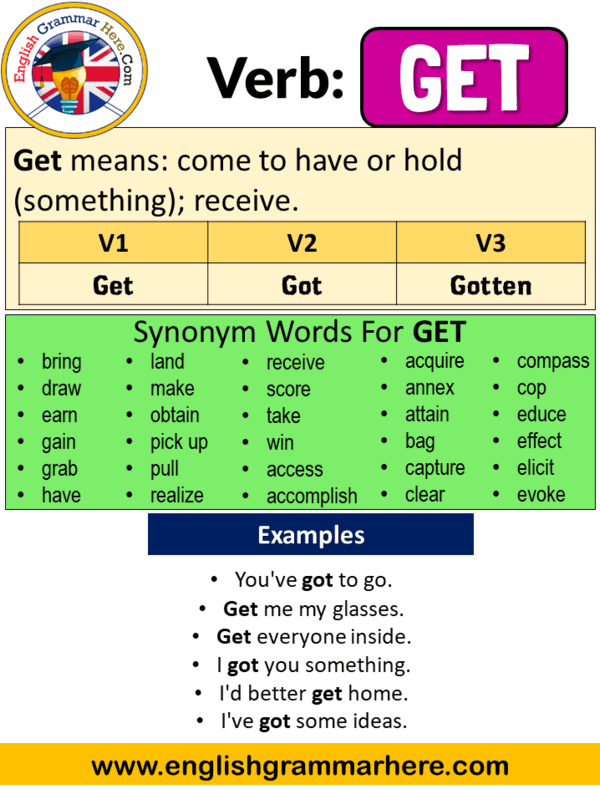
Get Past Simple, Simple Past Tense of Get, V1 V2 V3 Form Of Get

English Unite - Verbs Clip Art Image - Get

Get e Prepositions - Alumni Blog.